IT security threats continue to evolve in this digital economy. Complex environments make liabilities associated with inadequate security management more severe.
Hence, today’s enterprise needs its security team to deliver a higher level of protection at a significantly reduced cost.
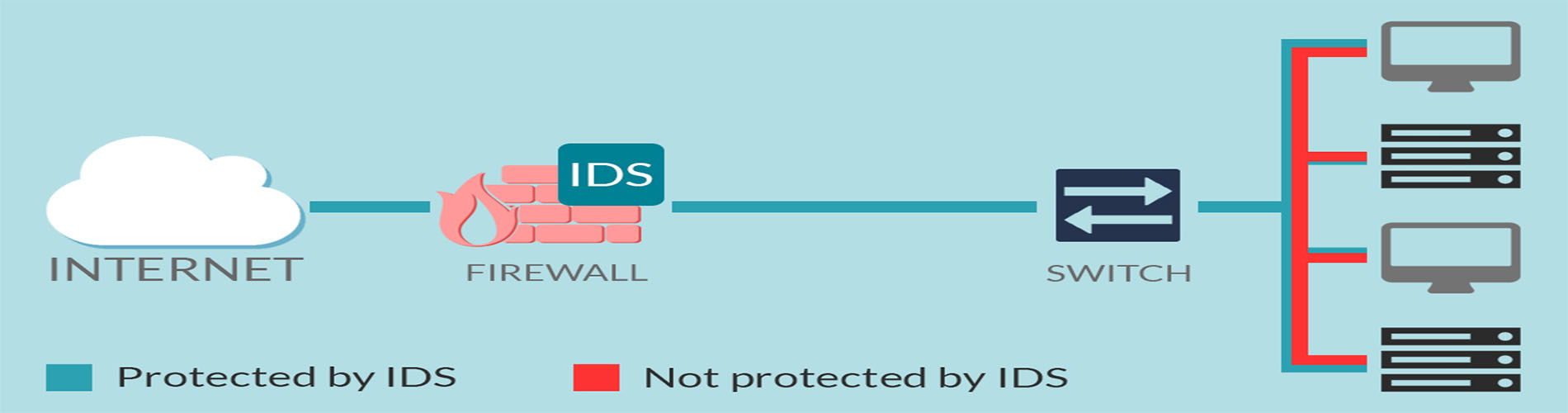
Our intrusion detection and prevention system (IDPS) service is designed to help you better secure your network from attacks and avoid system downtime. Our service helps you better manage costs and optimize the value of your existing security investments. We are expert at facilitating around-the-clock protection from threats and unauthorized intrusions.
It can be nearly impossible for many companies to staff a certified expert in every area of their environment.
At Unity Automation Services our engineers and consultants are highly-certified subject-matter experts. We offer 24/7, 365 monitoring and services including weekends, evenings, and holidays.
Our trained experts can provide the knowledge needed to solve your rigid technology challenges with our attentive, consultative approach. With Unity Automation in charge of your IDPS, IT professionals can shift their focus to higher priority items.
Unity Automation Services offers managed IT services in the following areas: remote monitoring and management, managed collaboration and contact center services, managed cloud services, backup and disaster recovery, and security as a service.
Our multistep approach to event analysis and attack recognition helps in improving your security posture. It also helps to deliver advanced attack detection.
Our services include device configuration and customizable reporting, as well as increased visibility into security events. Our solution combines around-the-clock threat monitoring and advanced policy management capabilities to help improve your security posture. In addition to supporting virtual private networks (VPNs), our service also supports a wide range of IDPS devices.
Hence comes the organization’s need to fine-tune their IDPS products when they first install them. That means properly configuring their intrusion detection systems. This helps them to recognize what normal traffic on their network looks like compared to potentially malicious activity.